










Mobiles and smart phones are the next major frontier for voice and speech technology. Voice biometrics will be at the heart of the user experience in a range of use cases and implementation scenarios. Rapidsoft Systems pre-crafted solutions allows you to integrate bio-metric solutions in any application of your choice. We supply tools and integrated solutions using industry's best voice autentication platforms. The turnkey solutions area available for financial, insurance and other industries that needs tested voice authentication system. Voice authentication can be integrated virtually any application where there is a need to add two factor authetication.
The following are just some of the ways that voice biometrics are being used on smartphones, mobile devices and tablets.
The smart phone environment is also a great way to integrate technology into any application. We provide the tools that make it easier getting an app up and running using our hosted development environment. The ecosystem is small, and crucially, there’s no need for an IVR.
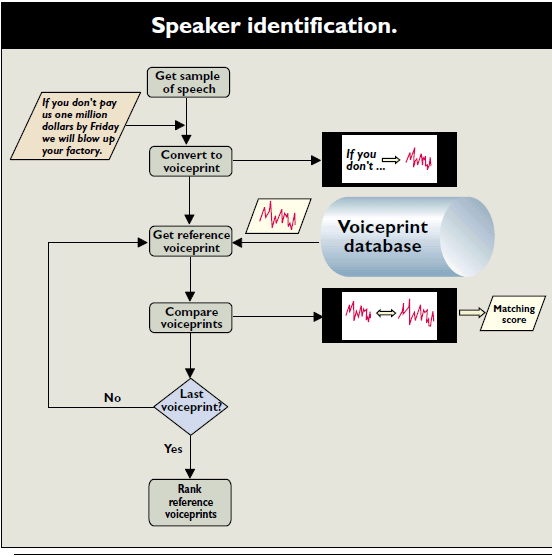
Voice Metrics Model
Biometric recognition, or biometrics, refers to the automatic identification of a person based on his/her anatomical (e.g., fingerprint, iris) or behavioral (e.g., signature) characteristics or traits. This method of identification offers several advantages over traditional methods involving ID cards (tokens) or PIN numbers (passwords) for various reasons: (i) the person to be identified is required to be physically present at the point-of-identification; (ii) identification based on biometric techniques obviates the need to remember a password or carry a token. With the increased integration of computers and Internet into our everyday lives, it is necessary to protect sensitive and personal data. By replacing PINs (or using biometrics in addition to PINs), biometric techniques can potentially prevent unauthorized access to ATMs, cellular phones, laptops, and computer networks. Unlike biometric traits, PINs or passwords may be forgotten, and credentials like passports and driver's licenses may be forged, stolen, or lost. As a result, biometric systems are being deployed to enhance security and reduce financial fraud. Various biometric traits are being used for real-time recognition, the most popular being face, iris and fingerprint. However, there are biometric systems that are based on retinal scan, voice, signature and hand geometry. In some applications, more than one biometric trait is used to attain higher security and to handle failure to enroll situations for some users. Such systems are called multimodal biometric systems.
A biometric system is essentially a pattern recognition system which recognizes a user by determining the authenticity of a specific anatomical or behavioral characteristic possessed by the user. Several important issues must be considered in designing a practical biometric system. First, a user must be enrolled in the system so that his biometric template or reference can be captured. This template is securely stored in a central database or a smart card issued to the user. The template is used for matching when an individual needs to be identified. Depending on the context, a biometric system can operate either in a verification (authentication) or an identification mode.
There are two different ways to recognize a person: verification and identification. Verification (Am I who I claim I am?) involves confirming or denying a person's claimed identity. On the other hand, in identification, the system has to recognize a person (Who am I?) from a list of N users in the template database. Identification is a more challenging problem because it involves 1:N matching compared to 1:1 matching for verification. Applications:
While biometric systems, particularly automatic fingerprint identification systems (AFIS), has been widely used in forensics for criminal identification, progress in biometric sensors and matching algorithms have led to the deployment of biometric authentication in a large number of civilian and government applications. Biometrics is being used for physical access control, computer log-in, welfare disbursement, international border crossing and national ID cards. It can be used to verify a customer during transactions conducted via telephone and Internet (electronic commerce and electronic banking). In automobiles, biometrics is being adopted to replace keys for keyless entry and keyless ignition. Due to increased security threats, the ICAO (International Civil Aviation Organization) has approved the use of e-passports (passports with an embedded chip containing the holder's facial image and other traits)Manage risk and ensure regulatory compliance with text-independent speaker verification that is secure, transparent and cost effective. Escalating incidents of identity theft, fraud and social engineering attacks continue to compromise existing data security measures. Traditional single-factor authentication approaches including passwords and challenge questions no longer provide the necessary safeguards for secure remote services. Biometric speaker verification technology uses the power of voice to provide the critical component in an effective multi-factor authentication solution.
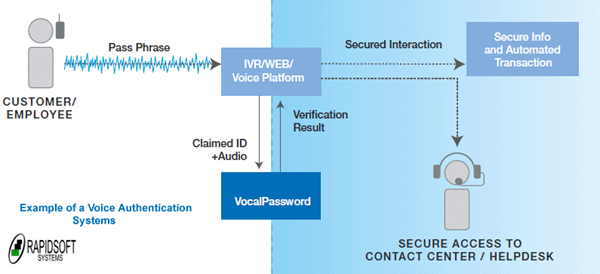
Voice Metrics Model
Our biometrics solution is built around a unique industry leading text-independent biometric speaker verification system that transparently verifies the identity of a speaker during the course of natural conversation. Totally content, language and accent independent, the voice system transparently retrieves the biometric voice characteristics required for verification within seconds, eliminating the need for cumbersome authentication questions. Moreover, voice biometrics enables contact centers to monitor incoming\outgoing calls and detect fraudulent activity by employing a watch list mechanism.
Rapidsoft Systems voice biometrics products are designed to meet the dynamic security needs of the world’s leading financial institutions, telecom service providers, healthcare providers, enterprises, and law enforcement and government agencies. Relying on the most advanced and accurate speaker verification technology available, organizations are empowered to improve security and ensure regulatory compliance, while reducing costs and delivering increased convenience to those they serve.
Based on robust biometric voice verification technology, Rapidsoft System’s products protect private information, improve efficiency, and enhance the secure delivery of remote services via contact centers and the Internet. We have spent significant resources in creating the most advanced, secure and easily deployed speaker verification platform available today. Serving as a common infrastructure to all voice verification products, the platform includes a rich set of features that address the various stakeholders involved in deployment-ensuring successful implementation.
Rapidsoft Systems provides a toolkit that enables you to replace the passwords used to access applications, your desktop, smart phones or websites with a voice biometric solution.
Since 2005, Rapidsoft Systems has specialized itself into the development of various mobile applications and has became a dominant force in those markets today.
The combination of our technical strength gives the general public access to the latest state of the
art technology for the exciting world of Mobile Commerce.
Contact us for more information about our biometrics solution.
Please contact us for more details on pricing and other custom features. We offer several pricing options - licensing and usage based pricings. Pricing based on the number of subscribers (starting as a low as $2/per consumer per month). Customization changes based on specific customer requirements can be done. Integration with end user systems is provided.